Access Control and Management Systems (ACMS) are integral components of modern security infrastructures, comprising both software and hardware solutions designed to regulate and monitor entry and exit points within various environments. The primary objective of ACMS is to register and restrict access for individuals or vehicles to designated areas, enhancing overall security and operational efficiency. This guide provides an in-depth look into the principles of operation, system components, integration with other security measures, and best practices for designing and implementing effective access control systems in accordance with American standards such as those from the National Fire Protection Association (NFPA) and the Occupational Safety and Health Administration (OSHA).
Access Control and Management Systems
Principles of Operation
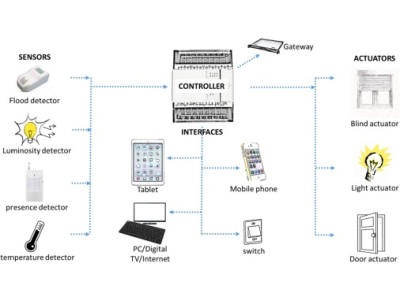
At its core, an Access Control and Management System (ACMS) functions by determining who is allowed to enter or exit specific areas within a facility. These systems are typically deployed at access points such as:
- Security Gates
- Doors
- Turnstiles
ACMS "decides" who can access certain areas based on predefined rules and permissions. Often, these systems are integrated with other security measures like video surveillance, intrusion alarms, and fire detection systems to provide a comprehensive security solution.
Components of Access Control Systems
A standard ACMS setup includes the following components:
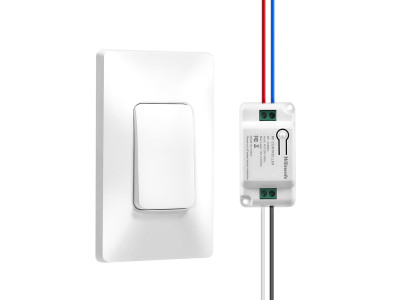
- Controllers: These devices store access codes and permissions, making decisions about granting or denying access based on the credentials presented.
- Identifiers: Devices used to identify individuals attempting to gain access, which can include:
- Keycards
- Fobs
- Biometric Identifiers (e.g., fingerprint scanners, iris scanners)
- Readers: Act as intermediaries between identifiers and controllers, transmitting identification data for verification.
- Barrier Devices: Physical devices that prevent unauthorized access, such as:
- Electric Strikes
- Magnetic Locks
- Turnstiles
- Boom Barriers
- Software: Manages the overall system, including user permissions, access logs, and integration with other security systems. Systems can be:
- Standalone: Simpler, often used in smaller facilities.
- Networked: More complex, allowing for centralized management and reporting across multiple locations.
- Additional Components:
- GSM Modules: For sending alerts and access logs via SMS.
- Remote Management Capabilities: Allowing administrators to manage the system over the internet.
Integration with Other Security Systems
Integrating ACMS with other security systems enhances overall protection and operational efficiency. Common integrations include:
- Video Surveillance: Allows for real-time monitoring and recording of access points, aiding in incident verification and response.
- Intrusion Alarms: Enhances security by providing alerts in case of unauthorized access attempts.
- Fire Alarm Systems: Ensures that access points can be automatically unlocked in case of an emergency, facilitating safe and swift evacuation.
Designing Access Control and Management Systems
Documentation Requirements
Effective design and implementation of ACMS require comprehensive documentation, including:
Technical Assignment (TA):
- Overview: General information about the project, objectives, and scope.
- Technical Requirements: Specific functionalities, response times, and integration needs.
- Source Data: Building plans, layouts, and existing security infrastructure details.
- Control Systems Requirements: Specifications for alarms, sensors, and management software.
- Equipment List: Brands and models of detectors, control panels, and other devices.
- Documentation Composition: Outline of all documents to be developed, including schematics, floor plans, and specifications.
Working Project:
- Explanatory Note: Detailed description of the building, including size, layout, and materials.
- Technical Solutions: Key design decisions and the rationale behind them.
- Calculations: Power requirements, load calculations, and other technical computations.
- Operational Procedures: Guidelines for system operation, safety protocols, and authorized personnel access.
- Technical Schematics and Drawings: Network plans, connection diagrams, and equipment layouts.
- Equipment Specifications: Comprehensive lists of all installed devices and materials.
- Budget Documentation: Cost estimates and resource allocation for equipment, installation, and configuration.
Acceptance Documentation:
- Acceptance Report for the ACMS: Formal confirmation that the system has been installed correctly and meets all specified requirements.
- Completion of Installation Work Act: Verification that installation work has been completed as per the project plan.
- Completion of Commissioning Work Act: Record confirming successful testing and commissioning of the system.
- Inventory of Installed Devices and Equipment: Detailed list of all ACMS components installed.
- Insulation Resistance Testing Protocol: Documentation of tests conducted to ensure electrical integrity.
- Input Control Protocol: Verification that all system inputs and functionalities are operational and correctly integrated.
Maintenance Documentation:
- Inspection Reports: Documenting the results of all inspections and tests.
- Maintenance Logs: Records of all maintenance and servicing performed on the ACMS.
- Testing and Verification Records: Documentation of system performance and reliability tests.
Device Selection and Integration
Selection of Security Detectors
Security Detectors are essential for monitoring unauthorized access and ensuring property protection. The main types include:
- Magnetic Contact Sensors: Monitor doors, windows, gates, and other entry points for unauthorized access.
- Motion Detectors: Utilize PIR (Passive Infrared), ultrasonic, or microwave technologies to detect movement in designated areas.
- Glass Break Detectors: Detect the sound or vibration of breaking glass, ideal for areas with large windows or glass doors.
- Vibration Detectors: Monitor structural vibrations indicative of forced entry attempts.
Addressable vs. Non-Addressable Detectors:
- Addressable Detectors: Each detector has a unique identifier, allowing precise localization of security breaches. Ideal for large or complex buildings.
- Advantages: Enhanced monitoring, easier scalability, advanced diagnostics.
- Disadvantages: Higher initial cost, more complex installation.
- Non-Addressable (Conventional) Detectors: Treat all detectors uniformly without individual identification. Suitable for smaller or budget-conscious installations.
- Advantages: Lower cost, simpler installation.
- Disadvantages: Limited localization, less flexible scalability.
Selection Criteria:
- Environmental Suitability: Choose detectors based on the specific environment (e.g., high-traffic areas, sensitive zones).
- Sensitivity and False Alarm Prevention: Select detectors with adjustable sensitivity to minimize false alarms without compromising security.
- Compliance: Ensure all detectors comply with NFPA 72 and other relevant standards.
Cable Networks and Wireless Communication Devices
Cable Networks
Types of Cables:
- Security-Resistant Cables: Essential for maintaining system integrity. Must comply with NFPA 72 standards for flame propagation and minimal smoke emission.
- Low-Smoke, Halogen-Free (LSFR/HFFR) Cables: Preferred for their minimal smoke and toxic gas emission during combustion.
Cable Routing and Installation:
- Separate Routing: Security alarm cables must not share conduits, trays, or cable bundles with power or data cables to prevent interference.
- Height Requirements: Install cables at least 7.5 feet above the floor or 4 inches below the ceiling for optimal performance.
- Protection from Damage: Use conduits or protective sleeves in areas where cables may be exposed to physical harm.
- Secure Fastening: Fasten cables securely at regular intervals (every 1 to 1.5 feet) using approved clamps or cable ties to prevent sagging and maintain organization.
Cable Testing and Certification:
- Insulation Resistance Testing: Ensure the electrical integrity of the cable lines through rigorous testing.
- Compliance Verification: Confirm that all cables used are certified and meet NFPA 72 and UL standards.
Wireless Communication Devices
Advantages of Wireless Systems:
- Flexibility: Easier installation in buildings where running cables is impractical or costly.
- Scalability: Simplifies the addition of new detectors without extensive wiring.
Considerations for Wireless Systems:
- Signal Reliability: Ensure robust communication protocols to prevent signal loss or interference.
- Power Supply: Use battery-operated devices with long battery life or integrate with existing power sources where feasible.
- Security: Implement encryption and secure communication methods to prevent unauthorized access or tampering.
Control Devices and Management Equipment
Control Panels
Types of Control Panels:
- Conventional Control Panels: Manage non-addressable detectors with predefined zones.
- Addressable Control Panels: Interface with addressable detectors, offering precise control and monitoring capabilities.
Selection Criteria:
- Capacity: Choose a control panel that can handle the current and future number of detectors and devices.
- Integration Capabilities: Ensure compatibility with other systems such as access control, video surveillance, and building management systems.
- User Interface: Opt for panels with intuitive interfaces for ease of use and maintenance.
Management Software
Features:
- Monitoring and Alerts: Real-time monitoring of system status and instant alerts in case of incidents.
- Reporting: Generate detailed reports on system performance, test results, and maintenance activities.
- Remote Access: Allow authorized personnel to manage and monitor the system remotely.
Security Considerations:
- Access Control: Implement role-based access to restrict system management to authorized users.
- Data Protection: Ensure that all transmitted and stored data is encrypted and secure from unauthorized access.
Integration with Other Systems
Benefits of Integration
- Enhanced Security: Combining access control systems with video surveillance, intrusion alarms, and fire detection systems provides comprehensive protection.
- Improved Response Times: Integrated systems can coordinate alerts and actions, enabling faster and more effective responses to incidents.
- Operational Efficiency: Streamlined management through unified control interfaces reduces complexity and improves system maintenance.
Integration Strategies
- Unified Control Panels: Use control panels that support multiple systems, allowing centralized management and monitoring.
- Communication Protocols: Employ standardized communication protocols (e.g., BACnet, Modbus) to ensure seamless interoperability between different systems.
- Automation: Implement automated responses, such as activating alarms, locking doors, or initiating surveillance measures based on specific triggers.
Challenges and Solutions
- Compatibility Issues: Ensure all integrated systems adhere to compatible standards and protocols to prevent communication breakdowns.
- System Complexity: Simplify system design by using modular components and scalable architectures to manage complexity effectively.
- Maintenance Coordination: Establish coordinated maintenance schedules and procedures to ensure all integrated systems remain functional and up-to-date.
Compliance with Standards and Regulations
Relevant Standards:
- NFPA 72 - National Fire Alarm and Signaling Code: Governs the design, installation, and maintenance of fire alarm and signaling systems.
- National Electrical Code (NEC): Regulates the electrical aspects of alarm system installations.
- UL Standards: Provide safety and performance requirements for fire alarm and security alarm devices and components.
- OSHA Standards (29 CFR 1910): Includes fire safety regulations for workplaces, covering the installation and maintenance of fire alarm systems to protect employees.
- Local Building Codes: Additional requirements specific to your locality must also be adhered to for compliance and safety.
Key Compliance Points:
- Detector Placement: Follow guidelines for placement distances from ceilings, walls, and each other to ensure optimal detection.
- Cable Routing: Maintain required separations from power lines and other potential sources of interference.
- System Integration: Ensure all detectors and devices are correctly integrated with the central control panel for coordinated alerting.
- Documentation and Certification: Keep detailed records of installations, testing, and compliance certifications to validate adherence to standards.
Final Thoughts
Implementing effective Access Control and Management Systems (ACMS) is essential for enhancing the security and operational efficiency of any facility. By adhering to established guidelines, selecting appropriate devices, ensuring robust communication networks, and integrating with other security measures, you can create a comprehensive protection solution that safeguards property and lives.
Key Takeaways:
- Strategic Device Selection: Choose the right types of detectors and identifiers based on environmental needs and system design (addressable vs. non-addressable).
- Robust Cable Networks: Implement fire-resistant cables with proper routing, separation from power lines, and secure fastening to maintain system integrity.
- Reliable Communication: Decide between wired and wireless communication methods based on building layout, budget, and scalability requirements.
- Effective Control Devices: Utilize advanced control panels and management software for centralized monitoring and management.
- Seamless Integration: Integrate access control systems with other security and safety systems to enhance overall protection and response capabilities.
- Compliance with Standards: Adhere strictly to NFPA 72, NEC, OSHA standards, and other relevant codes to ensure system legality, effectiveness, and reliability.
- Professional Expertise: Engage certified security system engineers and installers to design and implement systems that meet all safety and regulatory requirements.
- Ongoing Maintenance: Implement regular maintenance and testing protocols to sustain system performance and compliance over time.
For expert assistance in designing access control and management systems, selecting appropriate detectors, or accessing comprehensive project documentation, visit safsale.com. Our specialists are ready to help you create and implement reliable, compliant, and effective access control systems tailored to your specific needs.