Access Control and Management Systems (ACMS) are essential for regulating and monitoring entry and exit points within various environments. Understanding the structure and schematics of ACMS is crucial for designing effective security solutions that meet organizational needs. This guide delves into the components, structural configurations, and schematic representations of ACMS, aligning with American standards and best practices.
Structure and Schematic of ACMS
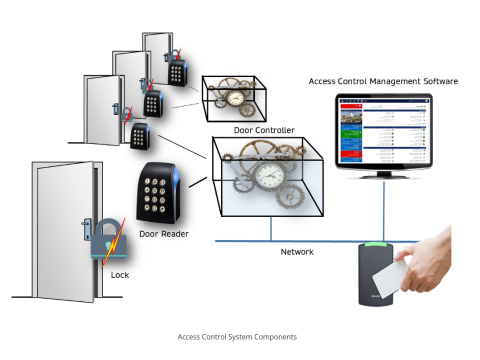
Components of Access Control and Management Systems (ACMS)
The core components of ACMS include:
- Locking Devices: Such as locks and strikes that secure entry points.
- Barrier Devices: Including turnstiles, gates, and bollards that control pedestrian and vehicular access.
- Controllers: Manage access permissions and process identification data.
- Identification Devices: Readers of various types and technologies that authenticate users.
- Control Panels or Servers: Central units that oversee the entire system.
- Power Supplies: Provide necessary electrical power to system components.
Additionally, ACMS may incorporate:
- Door Position Sensors: Monitor the open or closed status of doors.
- Exit Buttons: Allow users to manually request exit.
- Other Auxiliary Devices: Enhance system functionality and security.
Common ACMS Components Explained
- Locking Devices:
- Electric or Electromagnetic Locks: Secure doors electronically, allowing controlled access.
- Barrier Devices:
- Turnstiles and Bollards: Regulate the flow of people and vehicles, often used in high-traffic areas like company entrances or parking lots.
- Controllers:
- Standalone Controllers: Operate independently without centralized management.
- Networked Controllers: Integrated into a central management system, allowing for comprehensive control and monitoring.
- Identification Devices:
- Card Readers: Utilize RFID or NFC technology for contactless access.
- Biometric Readers: Employ fingerprint, facial, or iris recognition for secure identification.
- Control Panels or Servers:
- Central Management Units: Coordinate all system operations, handle data storage, and manage user permissions.
- Power Supplies:
- Primary and Backup Power Units: Ensure continuous system operation, even during power outages.
Standard ACMS Structure
1. Standalone ACMS Structure
A Standalone Access Control System operates independently without centralized management. This setup is ideal for controlling access to one or a few doors or rooms. The typical structure includes:
- Controller: Stores access codes and permissions locally.
- Lock: Electromagnetic or electromechanical, secured to the door.
- Power Supply: Provides necessary power to the controller and lock.
- Reader and Exit Button: Facilitate user identification and exit.
Schematic Diagram for Standalone ACMS:
Figure 1: Standalone Access Control System Schematic
Legend:
- Electromagnetic Lock
- Controller
- Reader
- Power Supply
- Exit Button
In scenarios requiring two-way access control, a second reader replaces the exit button (see Figure 1B).
Enhanced Standalone Structure:
Figure 1B: Two-Way Standalone Access Control System Schematic
Use Cases:
- Hotel rooms
- Office entrances
2. Networked ACMS Structure
A Networked Access Control System features a more complex structure, integrating multiple components under a centralized management system. This setup is suitable for larger facilities requiring comprehensive access control across various zones.
- Central Control Panel or Server: Manages all access points and stores user data.
- Multiple Controllers: Handle access requests from different zones.
- Advanced Locking and Barrier Devices: Secure multiple entry points.
- Integration Modules: Connect ACMS with other security systems like fire alarms and video surveillance.
Schematic Diagram for Networked ACMS:
Figure 2: Networked Access Control System Schematic
Functionalities of Networked ACMS:
- Zone Management: Organize areas into different access zones.
- Event Logging: Record access events for auditing and security analysis.
- Access Level Differentiation: Assign varying access permissions based on user roles.
- Integration Capabilities: Seamlessly connect with other security systems for enhanced protection.
Example System:
- ISB "Orion" by NPO "Bolide": Managed via the S-2000M panel or the "Orion" Automated Workstation (ARM).
Functionalities and Purpose of ACMS
- Access Regulation: Control who can enter specific areas based on predefined permissions.
- Authentication: Verify user identities through various identification methods.
- Integration: Work alongside other security systems to provide a unified security solution.
- Monitoring and Reporting: Track access events and generate reports for security audits and operational insights.
ACMS in Security Operations
ACMS and Security Systems Integration
Integrating ACMS with other security systems enhances overall protection and operational efficiency:
- Fire Alarm Systems: Automatically unlock access points during emergencies to facilitate safe evacuation.
- Intrusion Alarms: Coordinate with ACMS to alert security personnel of unauthorized access attempts.
- Video Surveillance: Provides visual verification of access events and assists in identifying individuals.
Roles and Limitations of ACMS in Security
- External Security: Prevent unauthorized individuals from accessing protected areas.
- Internal Security: Detect and monitor potential internal threats or misuse by employees.
- Incident Analysis: Utilize access logs and surveillance footage to investigate security breaches or internal misconduct.
Limitations:
- ACMS is not designed to perform engineering protection functions, such as resisting forced entry or tampering.
- Requires integration with robust physical security measures (e.g., secure locks, surveillance cameras) to provide comprehensive security.
Compliance with Standards and Regulations
Relevant Standards:
- NFPA 72 – National Fire Alarm and Signaling Code: Governs the design, installation, and maintenance of fire alarm and signaling systems, including aspects related to ACMS integration.
- National Electrical Code (NEC): Regulates the electrical aspects of alarm system installations to ensure safety and compliance.
- UL Standards: Provide safety and performance requirements for security alarm devices and components.
- OSHA Standards (29 CFR 1910): Include fire safety regulations for workplaces, covering the installation and maintenance of fire alarm systems to protect employees.
- Local Building Codes: Additional requirements specific to your locality must also be adhered to for compliance and safety.
Key Compliance Points:
- Detector Placement: Follow guidelines for placement distances from ceilings, walls, and each other to ensure optimal detection.
- Cable Routing: Maintain required separations from power lines and other potential sources of interference.
- System Integration: Ensure all detectors and devices are correctly integrated with the central control panel for coordinated alerting.
- Documentation and Certification: Keep detailed records of installations, testing, and compliance certifications to validate adherence to standards.
Final Thoughts
Implementing effective Access Control and Management Systems (ACMS) is essential for enhancing the security and operational efficiency of any facility. By adhering to established guidelines, selecting appropriate devices, ensuring robust communication networks, and integrating with other security measures, you can create a comprehensive protection solution that safeguards property and lives.
Key Takeaways:
- Strategic Device Selection: Choose the right types of detectors and identifiers based on environmental needs and system design (addressable vs. non-addressable).
- Robust Cable Networks: Implement fire-resistant cables with proper routing, separation from power lines, and secure fastening to maintain system integrity.
- Reliable Communication: Decide between wired and wireless communication methods based on building layout, budget, and scalability requirements.
- Effective Control Devices: Utilize advanced control panels and management software for centralized monitoring and management.
- Seamless Integration: Integrate ACMS with other security and safety systems to enhance overall protection and response capabilities.
- Compliance with Standards: Adhere strictly to NFPA 72, NEC, OSHA standards, and other relevant codes to ensure system legality, effectiveness, and reliability.
- Professional Expertise: Engage certified security system engineers and installers to design and implement systems that meet all safety and regulatory requirements.
- Ongoing Maintenance: Implement regular maintenance and testing protocols to sustain system performance and compliance over time.
For expert assistance in designing access control and management systems, selecting appropriate detectors, or accessing comprehensive project documentation, visit safsale.com. Our specialists are ready to help you create and implement reliable, compliant, and effective access control systems tailored to your specific needs.
Important Notice on Standards
All referenced documents and standards in this guide are provided for informational purposes only and should not be used as official publications. For authoritative guidelines and legal requirements, always consult the official standards organizations or regulatory bodies.